Make ISMS Scoping Look Easy
Turn complex scoping into quick wins with smart automation that gets you audit-ready fast.
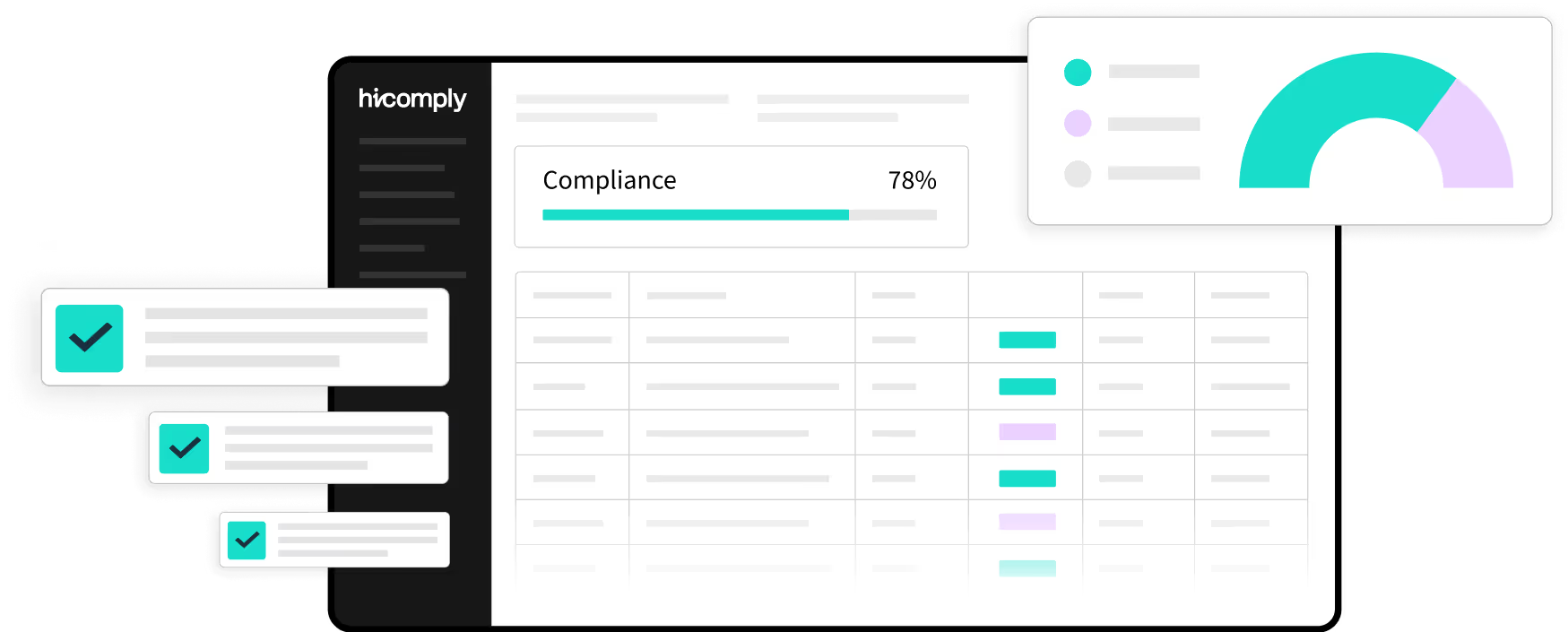
Request a demo to get started
With Hicomply, you get an all-in-one platform that automates and simplifies every step, helping you secure sensitive data, demonstrate accountability, and strengthen your business.











Say Goodbye to
Scoping Headaches
Let automation handle the heavy lifting while you focus on what matters.
Manual work crushing your time?
Creating an ISMS scope manually means spending weeks on tasks that should take hours. Teams get bogged down with complex requirements and endless document management.
- Weeks spent on manual requirements mapping
- Endless spreadsheets and disconnected tools
- Constant document updates and versions

Worried about compliance gaps?
A poorly defined scope can derail your entire certification process. Missing critical elements leads to failed audits and security vulnerabilities that cost you time and money.
- Missing critical audit requirements
- Overlooked security dependencies
- Incomplete compliance coverage

Racing against audit deadlines?
Every day spent on manual scoping is a missed opportunity. These delays don't just slow certification – they directly impact your ability to win business.
- Slower path to certification
- Missed business opportunities
- Compliance penalties

Your ISMS Scoping Powerhouse
Get everything you need to scope with confidence.
Benefits That Drive Real Results
See why teams choose Hicomply to crush their ISMS scoping goals
50% Faster Implementation
Skip the manual work with smart templates and automation that gets you audit-ready in half the time.
100% Compliance Rate
Generate perfect scope documents at the click of a button. No stress, no errors.
70% Less Manual Work
Let smart tools handle updates across all your documents while you focus on what matters.
10+ Standards Covered
From ISO 27001 to GDPR, handle every framework with confidence.
Teams Trust Us
Join leading businesses who've transformed their compliance journey.
5x Return in Year 1
Turn compliance investment into business advantage with faster certification.
*Based on real customer success. Your results could be even better.
Four Steps to Perfect Scoping
Get audit-ready faster with tools that make scoping simple.





See How Teams Win with Hicomply

“The Hicomply platform makes the process of auditing easier and reduces the need for extensive auditing meetings, saving us time and resource”


See How Easy Scoping Can Be
Transform your ISMS scoping from complex to confident in minutes.
Questions? We've
Got You Covered
Planning an audit? These will help.
For anything else, just ask.
What is an ISMS scope, and why is it important?
Your ISMS scope defines what parts of your organisation are covered by your information security management system (ISMS). It includes internal and external factors, dependencies, assets, and stakeholders that impact your security posture. A well-defined scope ensures compliance with ISO 27001 and helps avoid gaps that could lead to audit failures.
How does Hicomply simplify the ISMS scoping process?
We automate ISMS scoping with guided workflows, pre-built templates, and smart integrations. Our platform helps you map your organisation’s context, link dependencies, and generate an audit-ready scope document in minutes—eliminating manual work and reducing errors.
Can I customise the ISMS scope templates in Hicomply?
Absolutely. Our templates are fully customisable, allowing you to adjust scope parameters, add organisation-specific dependencies, and modify controls to align with your business structure and regulatory requirements.
Does Hicomply support multiple compliance frameworks?
Yes! Our platform covers ISO 27001, SOC 2, GDPR, PCI-DSS, and other major security frameworks. You can align your ISMS scope with multiple standards, ensuring a seamless compliance process across different regulatory requirements.
How does Hicomply help with audit readiness?
We maintain a single source of truth for all ISMS elements, so you’re always prepared for audits. Any updates made to your ISMS scope automatically cascade across policies, risk assessments, and compliance documents, eliminating last-minute preparation stress.
How long does ISMS scoping take with Hicomply?
Most organisations complete their ISMS scope 50% faster using our automation and guided workflows. What usually takes weeks can now be done in days.
Can multiple team members collaborate on Hicomply?
Yes. Our platform enables real-time collaboration, allowing different teams such as security, IT, and compliance to contribute to the ISMS scope simultaneously. This ensures that all critical factors are considered without back-and-forth email chains.
What happens if my business structure changes after setting the ISMS scope in Hicomply?
Our dynamic update feature ensures that any structural changes, such as new departments, processes, or security requirements, are reflected automatically across your ISMS scope and related policies. There is no need to manually edit multiple documents.
How does Hicomply ensure data security?
We follow the highest security standards, including ISO 27001-certified practices, encryption protocols, and access controls to protect your data. Our platform is designed to help you maintain compliance while keeping your sensitive information secure.
How do I get started with Hicomply?
It is easy. Book a demo to see how we can simplify your ISMS scoping and accelerate your compliance journey.





.jpg)
.jpg)
%20(1).jpg)

%20(1).png)



